Version 2.12.7 of Paid Memberships Pro is out with a single important security fix. Thanks to an anonymous source for the responsible disclosure of this issue.
On sites with certain setups or custom code, PMPro would sometimes make a request to the REST API that would accidentally result in the password and password2 (confirm password) fields entered at checkout showing up in plaintext in the web server’s access logs. To keep the accounts of users secure, both on your site and any other site they might have used the same password on, it is important that passwords never be stored in plaintext.
While only a subset of sites would have been affected by this, we recommend all sites update PMPro the latest version as soon as possible and read the rest of this post to determine if your site was affected. Affected sites should also delete or scrub their access logs and access log backups.
Please update Paid Memberships Pro from the plugins page of your WordPress dashboard. You can also get the latest version of PMPro here. We recommend that everyone upgrade as soon as possible.

What was happening?
When our Stripe-related JavaScript or custom code was calculating the updated checkout total, we were accidentally sending the password and other sensitive fields in a way that resulted in them being saved to the web server access logs.
How to Confirm Whether This Impacted Your Site
A number of things had to be in place for this issue to occur. The site must have been set up with all of the following:
- Using the Stripe gateway
- Using the onsite checkout option for Stripe
- Have the payment request buttons for Apple Pay and/or Google Pay enabled
- Had discount codes available on the site or were using the Payment Plans Add On
With this exact mix of components in place, new users that applied a discount code after filling in the password on the checkout form and then clicked to use Apple Pay or Google Pay would have had their password sent along with the REST API request and stored in the access logs.
Additionally, sites that used either of these two custom gists to update the total at checkout via JavaScript would also have been impacted by this issue.
To be safe, if any of the above was true on your site, you should assume that you may have some of your user’s private data stored in plaintext in your access logs.
To know for sure, you can use a command like the following from your server’s command line to look suspect entries in the access logs. (Update the path and filename to match the location of your actual access log. This will depend on your host.)
grep 'checkout_levels.*password=[^&]' ~/path-to-your/access.logIf you see output like the following, your site was affected by this issue.
123.45.68.9 - - [15/Nov/2023:16:40:48 -0500] "GET /wp-json/pmpro/v1/checkout_levels?level=20&checkjavascript=1&level=20&username=*****&password=*****&...If you do not see any output, or the output contains the word password but no text after the =, then it is unlikely that your site was affected by this issue.
How to Update and Protect Your Site
In addition to updating PMPro immediately, we also recommend that you (1) delete or scrub your web server’s access logs and access log backups and (2) notify any users that might have been affected by this issue.
The following is a bash script that will scan through an access log and (1) scrub any passwords found and (2) keep track of the related email address for any users scrubbed this way.
Note that it uses sed, a stream editor, for editing the files in place and grep for pattern matching. Make sure to back up your logs before running this script, as it will modify the files… but then delete those backups once you’ve confirmed the script ran properly.
If you have identified users affected by this issue, we recommend that you contact them to let them know what happened so they can change their password on your site and any other site where they may have used that same password.
You may want to send this email to all of your users.
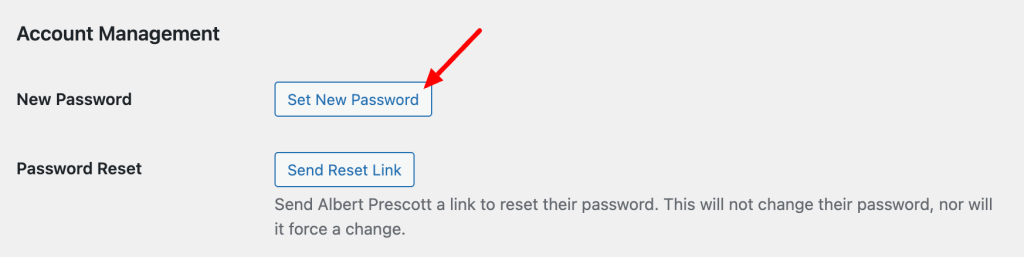
You may want to force a password reset for all of your users. You can do this by navigating to the affected users in the Users list in WordPress. Then, click the button to Set New Password.
If you have further questions or otherwise need help with anything related to this issue and update, please contact us or submit a ticket on our site. We are ready to help all users of PMPro affected by this issue to update and clean up any private data that might have been logged.